Blockchain Technology: Cryptocurrency Wallet Management
Table of Contents
Introduction
Blockchain technology and cryptocurrencies are rapidly developing as a new foundation for the digital economy. In particular, wallets, which are responsible for the secure storage and management of cryptocurrencies, play a crucial role in this new financial system.
This page provides a detailed explanation from the basics of blockchain technology to the types of cryptocurrency wallets and secure management methods. You can acquire the knowledge to securely store and transact with cryptocurrencies.
Blockchain Basics
What is Blockchain?
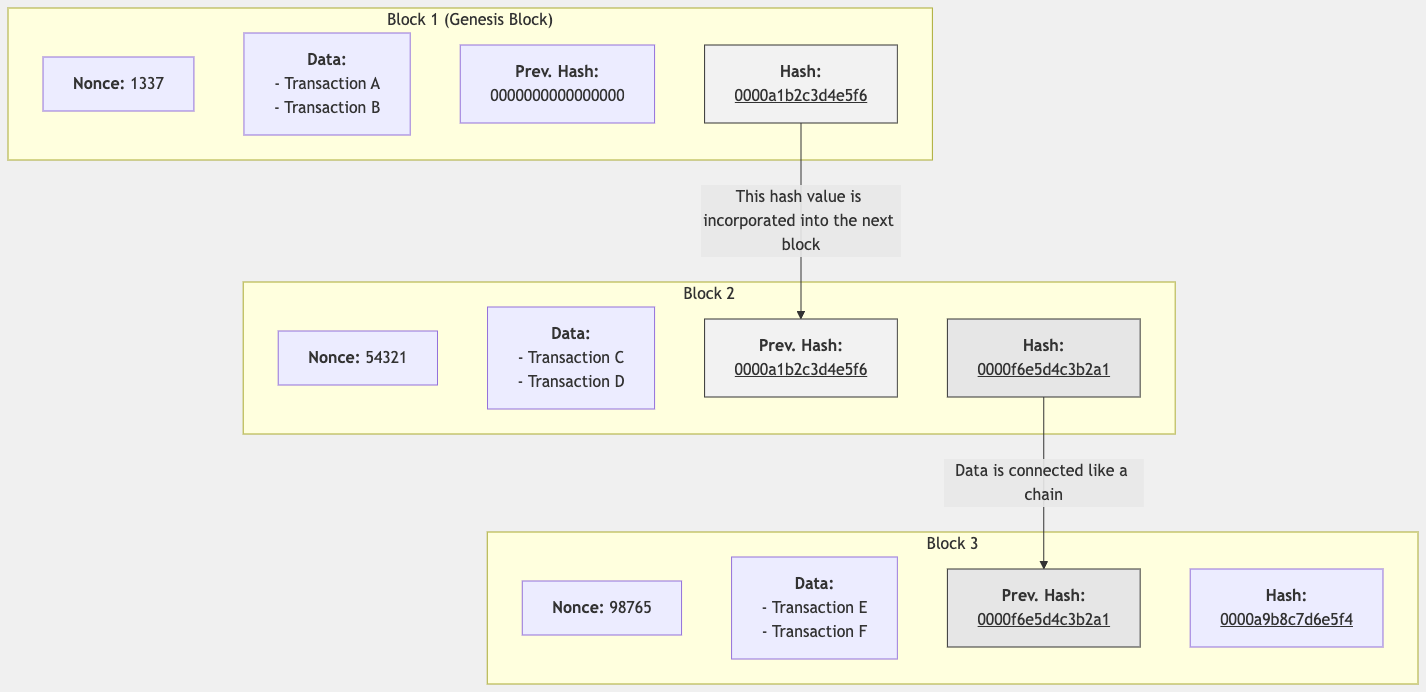
A blockchain is a distributed ledger technology that stores data in units called "blocks" and links them together using cryptographic techniques. Since each block contains the hash value of the previous block, it is extremely difficult to alter data once it has been recorded.
The main feature of this technology is its "decentralized" mechanism, where all participants share and verify data without the need for a central administrator. This creates a highly transparent and fault-tolerant system.
Structure of a Blockchain
Each block in a blockchain is mainly composed of the following elements:
1. Block Header
The block header contains important metadata for identifying and verifying the block. The main components are as follows:
- Previous Block Hash: By referencing the hash value of the immediately preceding block, it ensures the continuity of the blockchain. This means that if any block in the chain is altered, all subsequent blocks become invalid.
- Timestamp: Records the time the block was created. This ensures the chronological order of transactions and prevents issues like "double-spending".
- Merkle Root: A single hash value generated by combining the hash values of all transactions in the block in a binary tree structure. This allows for the efficient verification of large amounts of transaction data.
- Nonce: A special value that miners find during the "Proof of Work" calculation process. By changing this value, the hash of the entire block can be made to meet a specific condition (difficulty).
- Difficulty Target: Defines the condition that the block's hash value must meet. This adjusts the difficulty of block generation, ensuring blocks are created at a constant interval.
- Version: Indicates the version of the blockchain protocol being used. This allows for the management of protocol updates and forks.
2. Transaction Data
This is the body of the block and contains all the transaction information recorded in that block:
- Transaction Count: The total number of transactions included in the block. Due to block size limits, there is a maximum number of transactions that can be included in a single block.
- Individual Transactions: Each transaction includes the following information:
- Inputs: The source of the funds being used (outputs from previous transactions).
- Outputs: The destination address and amount of the funds being sent.
- Digital Signature: A signature for the sender to prove ownership of the funds.
- Transaction ID: A hash value that uniquely identifies the transaction.
- Coinbase Transaction: The first transaction in each block, which records the reward to the miner (newly issued coins and transaction fees). This is a special transaction that has no inputs.
3. Hash Value
A unique identifier generated from the entire block's data, which plays a central role in the security of the blockchain:
- Generation Method: Generated by passing all the information in the block header (previous block's hash, Merkle root, timestamp, nonce, etc.) through a cryptographic hash function (like SHA-256).
- Properties:
- Uniqueness: If the input data is changed even slightly, a completely different hash value is generated.
- Irreversibility: It is computationally impossible to reconstruct the original data from the hash value.
- Unpredictability: You cannot predict the hash value without knowing the input data.
- Role:
- Ensures the integrity of the block (prevents data tampering).
- Ensures the continuity of the blockchain (each block references the previous one).
- Forms the basis of the mining process (a competition to find a hash value that meets certain conditions).
The blocks are linked in a chain, with each block referencing the previous one, thus ensuring the continuity and integrity of the data.
Consensus Mechanisms
In a blockchain network, participants must reach a consensus on the addition of new blocks. This is an essential process for all participants in a decentralized system to share the same state of the blockchain.
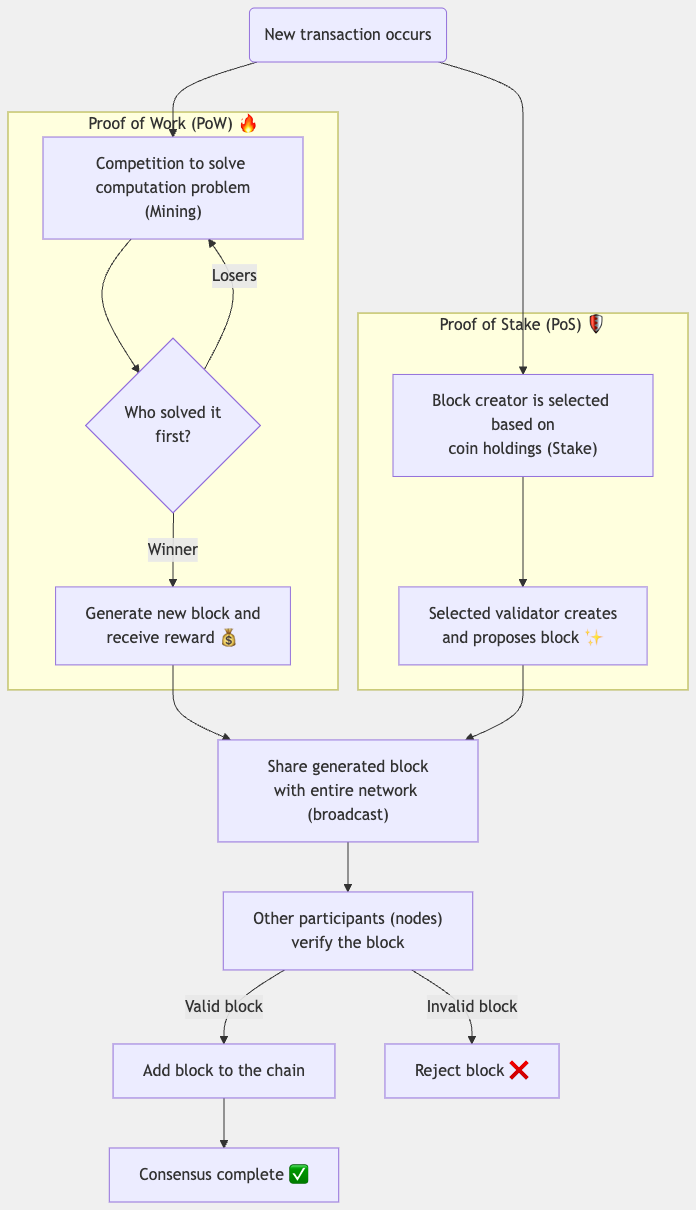
Basic Flow of Consensus
Consensus on a blockchain follows a basic flow like this:
- A new transaction occurs: A user creates a new transaction and sends it to the network.
- Processing by the consensus mechanism: It is processed based on the network's consensus mechanism (e.g., PoW or PoS).
- Block generation: A selected node (a miner or validator) generates a new block.
- Broadcasting: The generated block is shared across the entire network.
- Validation: Other nodes validate the block.
- Addition to the chain: Legitimate blocks are added to the blockchain, and invalid blocks are rejected.
- Consensus is reached: The entire network agrees on the new state.
Major Consensus Mechanisms
The main consensus mechanisms used in blockchains include the following:
Proof of Work (PoW)
This is the oldest and most widely used consensus mechanism, adopted by Bitcoin.
- Mechanism: Participants (miners) use computational resources to perform a task called "mining" to find a hash value that meets a specific condition.
- Process:
- Miners bundle unconfirmed transactions into a block.
- They repeatedly change the "nonce" in the block header and calculate the hash of the entire block until it meets a specific condition (difficulty).
- The first miner to find a hash that meets the condition earns the right to generate a new block and receives a reward (newly issued coins and transaction fees).
- Other miners lose the competition and move on to mining the next block.
- Features:
- High security: To alter the blockchain, an attacker would need to control more than 51% of the network's total computing power.
- High energy consumption: It consumes a large amount of electricity, raising environmental concerns.
- Scalability issues: Processing speed is limited, and there is a cap on transaction throughput.
- Examples of Adoption: Bitcoin (BTC), Litecoin (LTC), Monero (XMR), etc.
Proof of Stake (PoS)
A more environmentally friendly consensus mechanism developed to solve the high energy consumption problem of PoW.
- Mechanism: Participants (validators) increase their chances of earning the right to generate a block by staking (depositing as collateral) their cryptocurrency holdings.
- Process:
- To become a validator, you must stake a certain amount of cryptocurrency.
- Block generators are selected based on the amount of coins they hold (their Stake).
- The selected validator generates and proposes a block.
- Features:
- Energy efficiency: Power consumption is significantly lower compared to PoW.
- Economic security: An attacker would need to own a majority of the currency, and if an attack were to succeed, the value of their own assets would also fall, making it economically irrational.
- Higher scalability: Allows for faster transaction processing than PoW.
- Risk of centralization: "Whales" (large holders) who hold a large amount of currency could have significant influence.
- Examples of Adoption: Ethereum 2.0 (ETH), Cardano (ADA), Solana (SOL), Polkadot (DOT), etc.
Comparison of PoW and PoS
Here is a comparison table of the features of Proof of Work (PoW) and Proof of Stake (PoS), the main consensus mechanisms of blockchain:
| Comparison Item | Proof of Work (PoW) | Proof of Stake (PoS) |
|---|---|---|
| Basic Principle | Competition based on computational power | Selection based on the amount of currency held |
| Participants | Miners | Validators |
| Required Resources | High-performance computers, dedicated ASICs | Cryptocurrency holdings (stake) |
| Energy Consumption | Extremely high (comparable to a nation's power consumption) | Low (about 0.01% of PoW) |
| Security Model | A 51% attack requires a majority of the computational power | An attack requires owning a majority of the currency (economically irrational) |
| Scalability | Low (around tens of transactions per second) | Relatively high (thousands of transactions per second possible) |
| Decentralization | Tendency towards concentration in mining pools | Risk of concentration among large holders (whales) |
| Barrier to Entry | High (requires expensive equipment investment) | Medium (requires holding a certain amount of currency) |
| Examples of Adoption | Bitcoin (BTC), Litecoin (LTC), Monero (XMR) | Ethereum 2.0 (ETH), Cardano (ADA), Solana (SOL) |
Other Consensus Mechanisms
In addition to the above, various consensus mechanisms tailored to different characteristics and uses have been developed:
- Delegated Proof of Stake (DPoS): Token holders vote to elect a small number of "delegates" who are responsible for generating and validating blocks.
- Practical Byzantine Fault Tolerance (PBFT): Pre-selected validating nodes reach consensus through message exchange and voting.
- Proof of Authority (PoA): A system where specific trusted entities (authorities) generate blocks, used in enterprise private blockchains.
- Proof of Capacity (PoC): A system where the right to generate blocks is earned using hard disk free space.
- Proof of Elapsed Time (PoET): Each node is assigned a random waiting time, and the node whose waiting time ends first generates the block.
- Proof of History (PoH): A method that cryptographically proves the passage of time and ensures the order of transactions (adopted by Solana).
These consensus mechanisms each attempt to solve the security, scalability, and decentralization trilemma (the difficulty of optimizing all three simultaneously) with different approaches. Blockchain projects choose the optimal consensus mechanism according to their purpose and requirements.
Broadcasting and Validation
An important part of the consensus process is the broadcasting and validation of generated blocks. These are sequential processes that are essential for ensuring the integrity and reliability of the blockchain:
- Broadcasting:
- The node that generates a new block (a miner or validator) shares (broadcasts) that block to the entire network.
- Broadcasting is done through mechanisms like the gossip protocol, where information propagates from node to node in a chain reaction.
- Validation:
- Each node independently validates the received block.
- Validation includes checking the validity of transactions, the structure of the block, and its consistency with the previous block.
- If the block is deemed legitimate, it is added to their copy of the blockchain.
- If it is deemed invalid, it is rejected.
Below, we will explain the processes of broadcasting and validation in detail. First, let's look at the details of broadcasting in a blockchain network.
Details on Blockchain Broadcasting
Broadcasting is the process of propagating information to all participants (nodes) within a blockchain network. In a decentralized system like a blockchain, this broadcasting function plays an essential role in ensuring that all nodes share the same information and maintain a consistent state across the entire network.
Types and Purposes of Broadcasting
In a blockchain network, the following information is primarily broadcasted:
- Transaction Broadcasting: When a user creates a new transaction, it is first sent to the connected node and then broadcasted from there to other nodes. This allows unconfirmed transactions to propagate throughout the network, ready to be processed by miners or validators.
- Block Broadcasting: When a miner or validator generates a new block, that block is broadcasted to the entire network. Each node receives this block, validates it, and then adds it to its copy of the blockchain.
- Consensus Information Broadcasting: Depending on the consensus mechanism, information such as votes or approvals may also be broadcasted. For example, in PBFT, "prepare" or "commit" messages are broadcasted among nodes.
How Broadcasting Works
Broadcasting in a blockchain network is mainly done through the following process:
- Initial Propagation: Information (transactions or blocks) is first sent from the node that generated it to its directly connected "neighboring nodes".
- Flooding: When each node receives new information, it forwards it to all neighboring nodes to which it has not yet sent it. This causes the information to ripple through the entire network.
- Duplicate Prevention: Each node records the ID of the information it has already received to avoid processing it again.
- Validation: Nodes validate the received information, and if it is valid, they process it and forward it to other nodes. Invalid information is rejected and not forwarded.
Broadcasting Protocols
Various protocols are used in blockchain networks to achieve efficient broadcasting:
- Gossip Protocol: A method where a node tells a few randomly chosen neighboring nodes, and the information spreads in a chain reaction. It allows for efficient and robust broadcasting, but propagation can take time.
- Direct Broadcast: A method where a central node sends information directly to all participating nodes. It may be used in small-scale private blockchains.
- Hierarchical Broadcast: A method where nodes form a hierarchical structure, and information propagates from upper-level nodes to lower-level nodes. This helps to make large networks more efficient.
Challenges and Solutions for Broadcasting
Broadcasting in a blockchain network has the following challenges:
- Network Latency: Information propagation between geographically dispersed nodes
takes time, which can cause "forks" (temporary splits).
- Solution: The use of relay networks (dedicated networks that provide high-speed connections between nodes) and the optimal placement of geographically dispersed nodes are being implemented.
- Bandwidth Limitations: Transmitting large amounts of transaction or block data
requires significant bandwidth.
- Solution: Technologies like compact blocks (sending only the block header and unknown transactions) and mini-blocks (splitting a block into smaller parts for sending) have been developed.
- Scalability: As the number of nodes increases, the efficiency of broadcasting may
decrease.
- Solution: Technologies like sharding (dividing the network into multiple parts) and layer 2 solutions (processing off the main chain) are being introduced.
- Security Risks: Malicious nodes may broadcast fraudulent information.
- Solution: Measures such as the application of strict validation rules and reputation-based node selection are being taken.
Optimization of Broadcasting
To improve blockchain performance, the optimization of the broadcasting process is constantly being researched:
- Faster Block Propagation: Technologies like Bitcoin's "Compact Block Relay" (BIP 152) and Ethereum's "Fast Block Propagation" have significantly improved the speed of block propagation.
- Memory Pool Synchronization: A mechanism for efficiently synchronizing the pool of unconfirmed transactions between nodes reduces the transfer of duplicate data.
- Network Topology Optimization: Optimizing the connection structure between nodes improves the efficiency of information propagation.
An efficient broadcasting mechanism plays an important role in maintaining the balance of performance, security, and decentralization of a blockchain network. As technology evolves, faster and more efficient broadcasting methods continue to be developed.
The next step after broadcasting is the validation process for the received blocks or transactions. Below, we will explain this validation process in detail.
Details on Blockchain Validation
"Validation" in a blockchain is a core process for maintaining the reliability and integrity of the network. In a decentralized system, there is no central authority, so each participant (node) performs validation independently, which ensures the reliability of the entire system.
Significance and Role of Validation
Validation in a blockchain plays the following important roles:
- Prevention of Double-Spending: Prevents the same coin from being used multiple times.
- Elimination of Fraudulent Transactions: Prevents transactions that violate the rules from being recorded on the blockchain.
- Ensuring Data Integrity: Maintains the consistency and accuracy of the entire blockchain.
- Formation of Decentralized Consensus: Provides the basis for all participants to agree on the same state of the ledger without a central authority.
- Enhancement of Security: Protects the network from malicious attacks and tampering.
Types and Levels of Validation
Validation is performed at multiple levels in a blockchain:
- Transaction-Level Validation: Confirms the legitimacy of individual transactions.
- Block-Level Validation: Validates the overall structure and content of a block.
- Chain-Level Validation: Confirms the integrity of the entire blockchain.
Transaction Validation Process
The following items are checked during transaction validation:
- Syntax and Format Validation:
- Whether the transaction's data structure follows the correct format.
- Whether all required fields (input, output, signature, etc.) are present.
- Whether the transaction size is within the allowable range.
- Digital Signature Validation:
- Using the sender's public key to verify that the transaction's signature is valid.
- Verifying that the signature was truly created by the owner of the corresponding private key.
- Checking that the transaction data has not been tampered with after signing.
- Double-Spending Check:
- Checking that the input being used (UTXO) has not already been used in another transaction.
- Checking both the memory pool (pool of unconfirmed transactions) and the existing blockchain.
- Balance and Fee Validation:
- Whether the total amount of the inputs is greater than or equal to the total amount of the outputs (no insufficient balance).
- Whether the transaction fee (total inputs - total outputs) meets the minimum requirement.
- Script Execution and Validation:
- In systems like Bitcoin, executing the script included in the transaction to confirm that the conditions are met.
- In smart contract platforms, validating the execution result of the contract code.
Block Validation Process
The following items are checked during the validation of an entire block:
- Block Header Validation:
- Whether the block's hash value meets the current difficulty requirement (in the case of PoW).
- Whether the timestamp is within a reasonable range (not in the future, not older than the previous block).
- Whether the block size is within the allowable range.
- Whether the version number is compatible with the current protocol.
- Continuity Check with the Previous Block:
- Whether the "previous block's hash" included in the block header points to an existing block.
- Whether that block is part of the current longest chain (main chain).
- Merkle Root Validation:
- Whether the Merkle root calculated from all transactions in the block matches the one recorded in the header.
- This efficiently confirms that all transactions in the block have not been tampered with.
- Block Reward Validation:
- Whether the amount of the coinbase transaction (miner's reward) follows the current block reward rules.
- Whether all transaction fees are calculated correctly.
- Validation of All Transactions:
- Whether all transactions in the block are individually valid.
- Whether there are no contradictions between transactions within the block (e.g., double-spending the same input).
Technical Implementation of Validation
Various technical innovations have been implemented to make the validation process more efficient:
- Merkle Trees:
- A structure that combines the hash values of all transactions in a binary tree.
- Allows for the efficient verification of whether a specific transaction is included (O(log n) computational complexity).
- Allows light nodes that do not have the full block data to verify the existence of a specific transaction.
- Signature Aggregation:
- Improves computational efficiency by combining multiple signatures into one for verification.
- Uses technologies like Schnorr signatures or BLS signatures.
- Parallel Validation:
- Improves processing speed by validating multiple transactions simultaneously.
- Implementation of parallel processing utilizing multi-core processors.
Challenges and Countermeasures for Validation
The blockchain validation process has the following challenges and countermeasures:
- Scalability Issues:
- Challenge: As the number of transactions increases, validation takes longer, limiting throughput.
- Countermeasure: Addressed with technologies like layer 2 solutions (e.g., Lightning Network), sharding, and sidechains.
- Occurrence of Forks:
- Challenge: If multiple nodes generate different blocks at the same time, a temporary split in the chain (fork) occurs.
- Countermeasure: Resolved by fork selection algorithms like the "longest chain rule".
- Decrease in Validating Nodes:
- Challenge: The high cost of running a full node poses a risk of a decrease in the number of validating nodes.
- Countermeasure: Addressed by lightweight client protocols and improvements in incentive design.
- Threat of Quantum Computers:
- Challenge: The risk that quantum computers may be able to break current cryptography in the future.
- Countermeasure: Research and preparation for the implementation of quantum-resistant cryptography.
Importance and Future Prospects of Validation
The validation process is a fundamental element of blockchain technology, and its efficiency and robustness greatly affect the performance and security of the blockchain. The improvement of validation mechanisms remains an important research topic for the future development of blockchain technology.
New validation technologies are being developed that balance privacy protection and validation efficiency, such as Zero-Knowledge Proofs, STARKs, and SNARKs, as well as new consensus algorithms that achieve both decentralization and efficiency of validation. These technological innovations are expected to lead to the realization of faster, more secure, and privacy-protecting blockchains.
Cryptocurrency
What is Cryptocurrency?
Cryptocurrency is a digital currency that uses cryptographic techniques to ensure its security. It functions based on blockchain technology, without relying on central authorities like central banks or governments.
Main features of cryptocurrency:
- Decentralized: Operated on a peer-to-peer network without a central administrator.
- Anonymity: Transactions are public, but their link to personal information is limited.
- Cross-border Transfers: International transfers are possible without geographical constraints and at low cost.
- Tamper-resistant: Blockchain technology makes it difficult to alter transaction history.
Major Types of Cryptocurrencies
There are currently thousands of types of cryptocurrencies, but the most representative ones include:
- Bitcoin (BTC): The first cryptocurrency, with the largest market value. Also called "digital gold".
- Ethereum (ETH): Has smart contract functionality and also serves as a development platform for decentralized applications (DApps).
- Ripple (XRP): A cryptocurrency aimed at being an international money transfer system for financial institutions.
- Stablecoins: Cryptocurrencies whose value is pegged to fiat currencies like the US dollar (e.g., USDT, USDC).
- Altcoins: A general term for cryptocurrencies other than Bitcoin. Many have unique features and uses.
Cryptocurrency Wallets
What is a Wallet?
A cryptocurrency wallet is a tool for storing and managing cryptocurrencies. However, unlike a regular wallet, it does not physically store the cryptocurrency itself. In reality, it is a system that manages the private and public key pairs needed to access assets on the blockchain.
Main functions of a wallet:
- Sending and receiving cryptocurrencies
- Checking balances
- Displaying transaction history
- Secure storage of private keys
Types of Wallets
Cryptocurrency wallets are classified as follows based on their form and connectivity:
Classification by Connectivity
- Hot Wallet: A wallet that is connected to the internet.
- Web wallet: Accessible from a browser.
- Mobile wallet: Provided as a smartphone app.
- Desktop wallet: Software for a PC.
- Cold Wallet: A wallet that is not connected to the internet.
- Hardware wallet: Stores private keys on a dedicated device (e.g., Ledger, Trezor).
- Paper wallet: Stores private keys by printing them on paper.
Classification by Management Method
- Custodial Wallet: A third party (like an exchange) manages the private keys.
- Non-custodial Wallet: The user manages their own private keys.
Wallet Security
The security of a wallet is the most important matter for securely storing cryptocurrencies. The main security features include:
- Seed Phrase (Recovery Phrase): A sequence of usually 12 to 24 words used to restore a wallet.
- Password Protection: Restricts access to the wallet.
- Two-Factor Authentication (2FA): Provides an additional layer of authentication.
- Multi-signature: A mechanism that requires approval from multiple private keys.
The security level is generally considered to be highest in the order of cold wallet > non-custodial hot wallet > custodial wallet.
Key Management
Private and Public Keys
The core of a cryptocurrency wallet lies in the management of key pairs based on public-key cryptography.
- Private Key: A randomly generated number used to prove ownership of cryptocurrencies and to sign transactions. The private key should be kept literally "private," as anyone who knows it can use the associated cryptocurrency.
- Public Key: A key that is mathematically derived from the private key and is used to receive cryptocurrencies by sharing it with others.
- Address: An even shorter form generated from the public key, used as the actual destination for sending funds.
This mechanism creates a secure system where only the person with the private key can use the assets, while knowing only the public key or address does not grant access to the assets.
Key Storage Methods
The method of storing the private key is the most important factor affecting the security of cryptocurrencies. The main storage methods include:
- Hardware Wallet: The most secure method, which stores the private key on a dedicated device and performs signing offline.
- Software Wallet: Stores the private key as an encrypted digital file.
- Paper Wallet: Stores the private key by physically printing it on paper.
- Brain Wallet: Generates a private key from an easy-to-remember phrase (not recommended due to high security risks).
- Custodial Service: An exchange or wallet provider manages the private key.
When storing a large amount of cryptocurrency, it is recommended to use cold storage (offline storage).
Key Recovery and Backup
If you lose your private key, you will permanently lose access to the associated cryptocurrency. Therefore, proper backup and recovery methods are essential:
- Seed Phrase (Mnemonic Phrase): A sequence of 12 to 24 words based on standards like BIP39, used to restore the private key. This phrase must be stored in a safe place.
- Distributed Backup Storage: Storing copies of the seed phrase in multiple secure locations.
- Shamir's Secret Sharing: An advanced method that splits the seed phrase into multiple "shares," which can be used to restore it if a certain number of shares are available.
When creating backups, you also need to consider the risk of physical damage (fire, flood, etc.) and theft. It is also important to check the condition of the backup periodically.
Wallet Management Best Practices
Here are the best practices for securely managing your cryptocurrencies:
- Use multiple wallets: Use a hot wallet for daily small transactions and a cold wallet for long-term storage separately.
- Use strong passwords: Use a long, complex password for your wallet that is not shared with other services.
- Enable two-factor authentication: Set up two-factor authentication for your wallets and accounts whenever possible.
- Keep software up to date: Regularly update your wallet software and device firmware.
- Store multiple backups: Store backups of your seed phrase in multiple secure locations.
- Beware of phishing scams: Check the URL of official websites and do not click on suspicious links.
- Perform a small test transaction: When sending to a new address, first check if you can send a small amount correctly.
- Avoid using public Wi-Fi: Conduct cryptocurrency transactions in a secure network environment.
- Be mindful of privacy: Do not disclose your cryptocurrency holdings on social media.
By combining these measures, you can significantly improve the security of your cryptocurrencies.
Common Issues and Solutions
Here are common issues that occur while using cryptocurrency wallets and their solutions:
Loss of Private Key
Issue: If you lose your private key or seed phrase, you will lose access to the associated
cryptocurrency.
Solution:
- Store your seed phrase in a safe place and check your backup periodically.
- Store backups in multiple locations.
- If you use a custodial service, check the account recovery options for that service.
Sending Mistakes
Issue: If you send funds to the wrong address or to an incompatible network, the funds may
be lost.
Solution:
- Check the address multiple times before sending.
- Perform a small test transaction to a new destination for the first time.
- Use a QR code to prevent manual entry errors.
- Confirm that the destination cryptocurrency and network are correct.
Phishing Scams
Issue: Your private key may be stolen by fake wallet sites or fraudulent apps.
Solution:
- Download wallets directly from official websites or app stores.
- Enter the URL directly or use a bookmark.
- Do not click on links in suspicious emails or messages.
- Check the SSL certificate of the wallet's official website.
Malware Infection
Issue: There is malware that monitors clipboard operations and replaces cryptocurrency
addresses.
Solution:
- Use reputable security software.
- Re-check the address in the clipboard before sending.
- Use a hardware wallet for important transactions.
- Keep your OS and software up to date.
Exchange Hacking
Issue: Cryptocurrency exchanges can be hacked, and the assets stored there can be
stolen.
Solution:
- Move assets for long-term storage from an exchange to your own wallet.
- Choose an exchange with robust security measures.
- Set up two-factor authentication for your exchange account.
By preparing for these issues in advance, you can manage your cryptocurrencies securely. If a problem occurs, it is important to respond calmly and, if necessary, seek advice from experts.